Cybercriminals lure content creators with promises of cutting-edge AI wizardry, only to attempt to steal their data or hijack their devices instead
17 Apr 2025
•
,
3 min. read

The craze around generative AI tools isn’t just reshaping industries – it also provides fertile ground for cybercriminals, who are always quick to piggyback on the allure of the latest big thing in tech. So what if, instead of downloading an AI‑generated video from CapCut or another similar tool, you had your data stolen or gave control of your computer to a stranger?
The threat isn’t hypothetical – security researchers have previously observed campaigns that exploited CapCut’s popularity to distribute multiple infostealers and other malware. Let’s now look briefly at another campaign that’s targeting people interested in AI-powered content by promising premium versions of popular software such as CapCut, Adobe Express and Canva.
The art of the lure
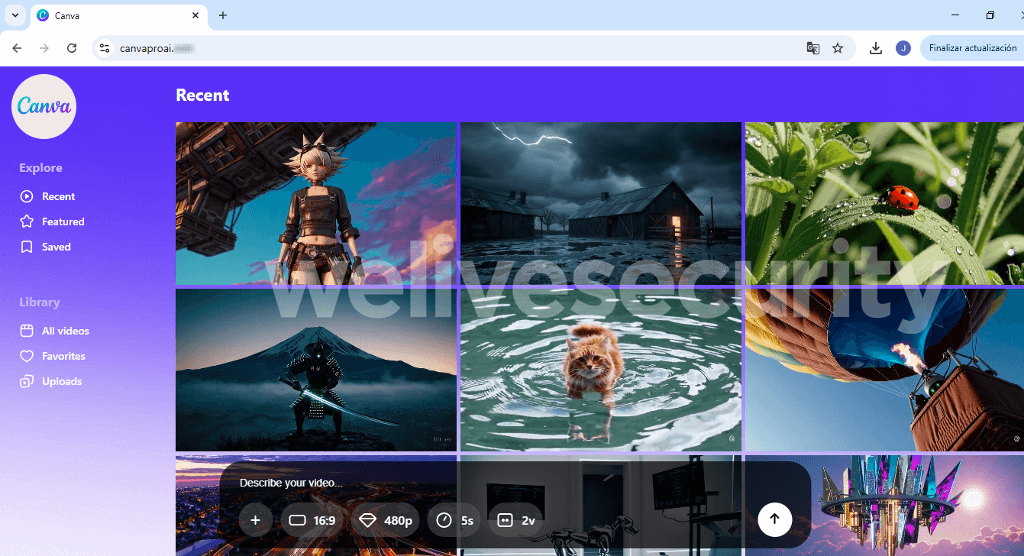
The example below, spotted by X user g0njxa, shows a website that impersonates CapCut, a tool often used by TikTok creators, and purports to be CapCut’s premium version. (Note that the actual premium version is called “CapCut Pro” or referred to simply as “Pro” on the website, not “CapCutProAI” as in the screenshot.)
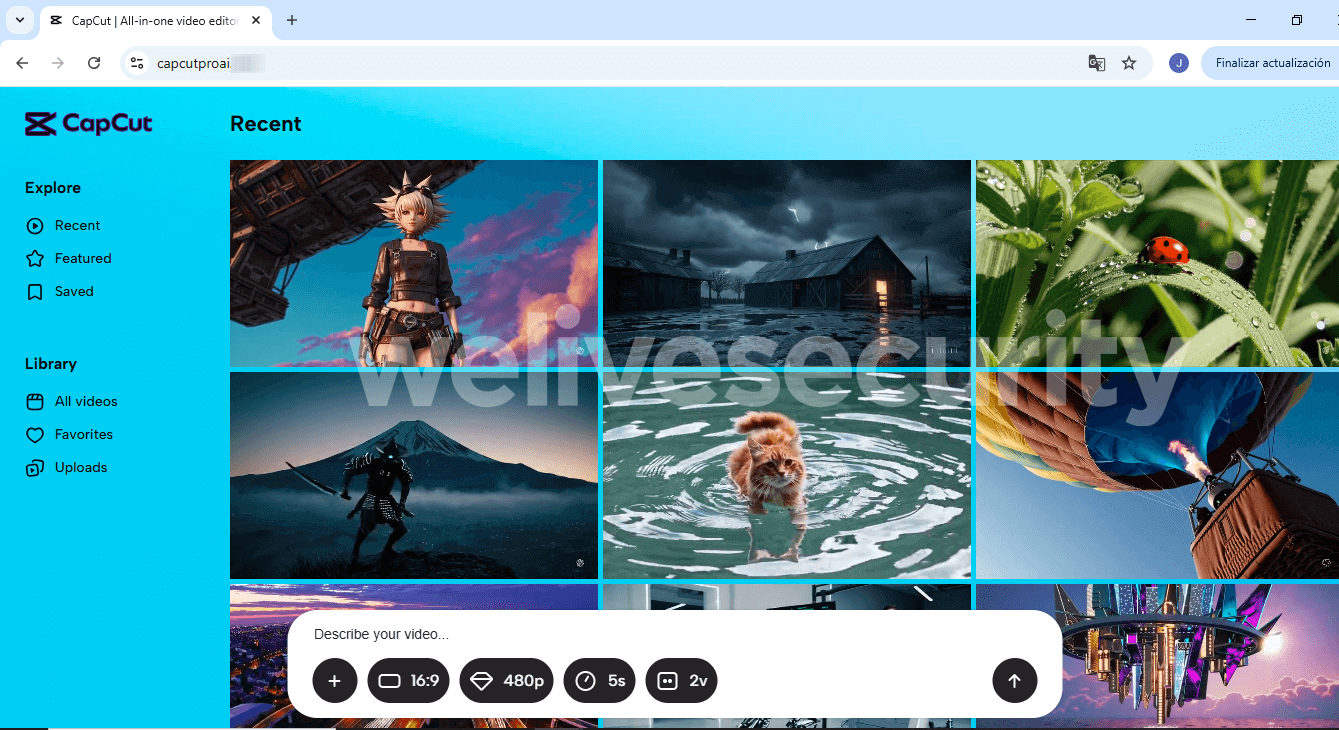
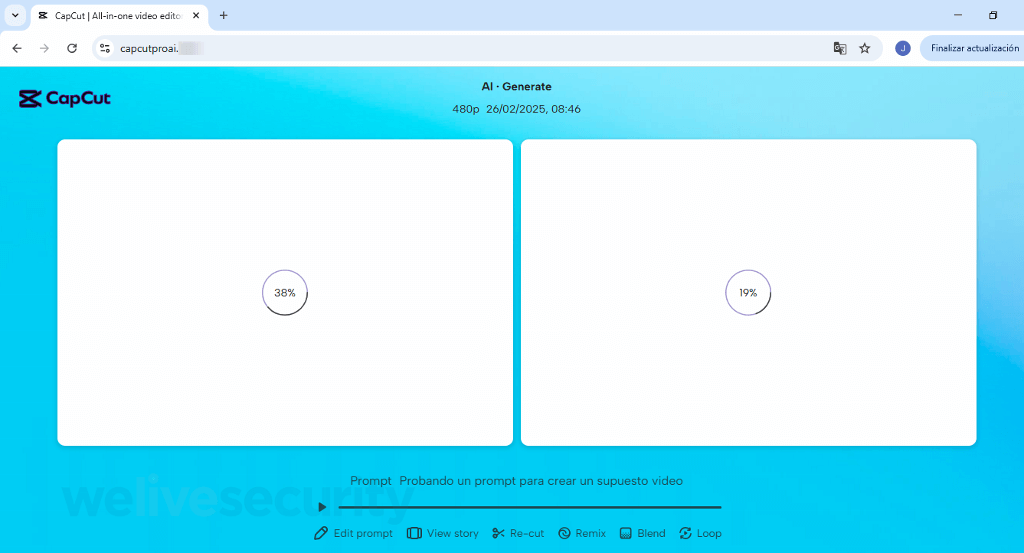
After you land on the fake site, you’re asked to enter a prompt or upload a reference file. If you comply, the site will mimic processing the request.
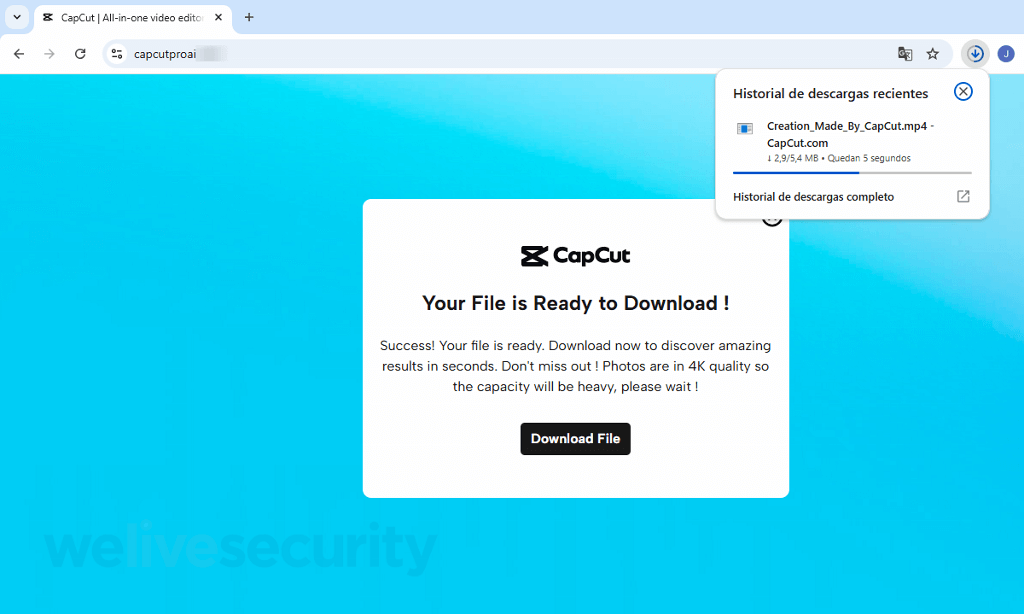
Once the anticipation is built and the trap is sprung, you’re prompted to download your shiny new “creation”. Needles to say, the file, called Creation_Made_By_CapCut.mp4 – CapCut.com, is far from what it purports to be. In reality, it’s an executable for remote access software. Fast forward a few clicks and, unless other safeguards kick in, you might be surrendering control of your device to crooks.
Here are two more sites that masquerade as the real deal and are part of the same campaign:
Faraway, so close
For context, while legitimate remote access tools, such as ConnectWise ScreenConnect, TeamViewer and AnyDesk, are invaluable for IT professionals providing technical support, in the wrong hands they can be misused to take over control of your computer for malicious ends. These include data theft, installation of ransomware or other malware, and using the compromised machine as a launch pad for attacks at other devices.
These kinds of threats also loom large on corporate networks, as threat actors can, for example, distribute portable, self-contained executables for legitimate remote monitoring and management (RMM) software that circumvents admin privileges and obviates the need for full software installation.
“Most remote control applications come with the option to generate a preconfigured executable to connect to a specific IP address or user. This is useful for remote assistance, but also for attackers. The victim simply has to open the file, and in a couple of clicks, they may unwittingly give control of their computer to a cybercriminal,” says Martina López, a security researcher with ESET’s lab in Latin America.
Word to the wise
A few simple steps will go a long way toward keeping you safe:
- When downloading new software, make sure to get it from the legitimate source, typically the publisher’s official website
- Avoid clicking on unsolicited links in email or social media messages that often claim to lead to such websites – the messages may be fake
- The same goes for ads – you’re better off navigating to the website directly by typing it in your browser or searching for it (with a critical eye, though) in your search engine of choice
- Inspect the website’s URL – software makers don’t normally sport various oddball extensions in URLs or sneaky “alternate” versions (think “CapCutProAI”)
- Make sure your operating system, browser, and other software are up to date to protect against known vulnerabilities
- Use multi-layered security software, as well as stick to other basic cybersecurity hygiene practices, such as strong and unique passwords and enabling two-factor authentication on all your online accounts
Needless to say, this is neither the first nor last time CapCut users have been targeted by cybercriminals, and these examples just show that cybercriminals are always eager to exploit trust and the latest big thing in tech.
The good news is that that while these ploys are often slick, they’re not invincible. Your vigilance is your best shield against scammers’ tactics.


